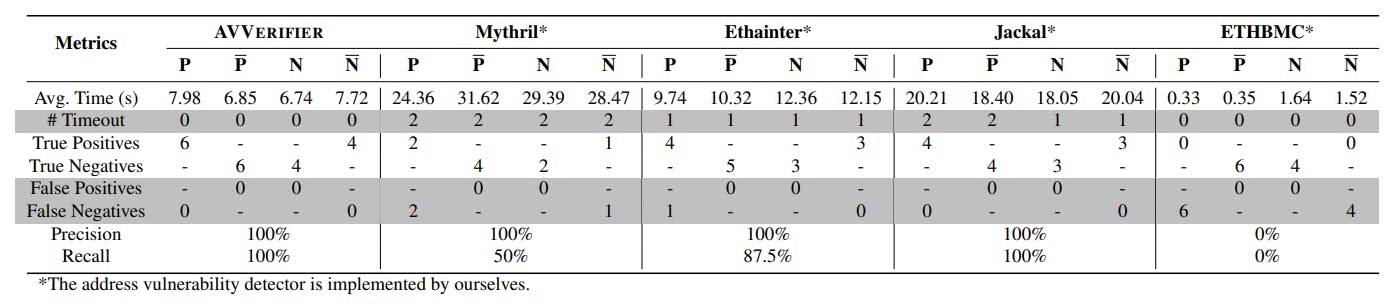
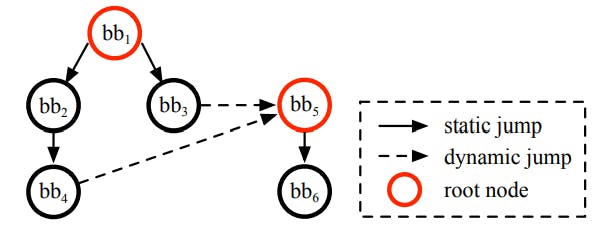
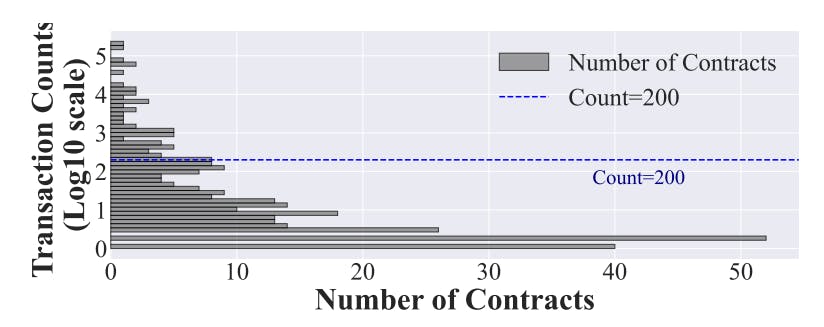
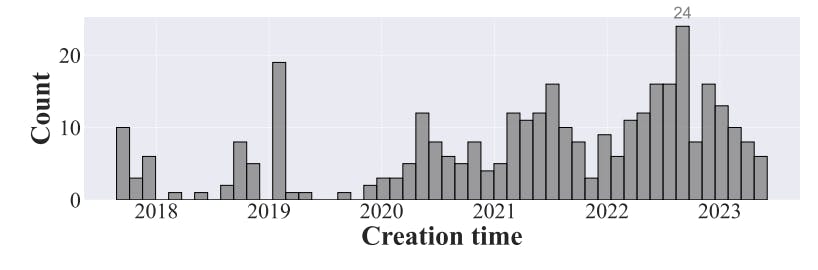
#vulnerability-detection
#vulnerability-detection
[ follow ]
#smart-contracts #ethereum #avverifier #cybersecurity #blockchain-security #static-analysis #dynamic-analysis
Privacy technologies
fromTechzine Global
5 months agoGoogle's AI Big Sleep discovers twenty new security vulnerabilities in open source
AI-powered vulnerability detector Big Sleep identified twenty new vulnerabilities in open-source software, leveraging collaboration between Google DeepMind and Project Zero.
fromThe Hacker News
6 months agoGoogle AI "Big Sleep" Stops Exploitation of Critical SQLite Vulnerability Before Hackers Act
An attacker who can inject arbitrary SQL statements into an application might be able to cause an integer overflow resulting in read off the end of an array.
Artificial intelligence
Tech industry
fromZero Day Initiative
8 months agoZero Day Initiative - CVE-2024-44236: Remote Code Execution vulnerability in Apple macOS
Monitor specific ports to detect attacks exploiting this vulnerability.
Verify ICC Profile file transfers for suspicious characteristics to prevent potential attacks.
[ Load more ]