"A TCSC can be well qualified for the role of decentralized vote manager in an e-voting system, ensuring confidentiality, neutrality, auditability, and accountability."
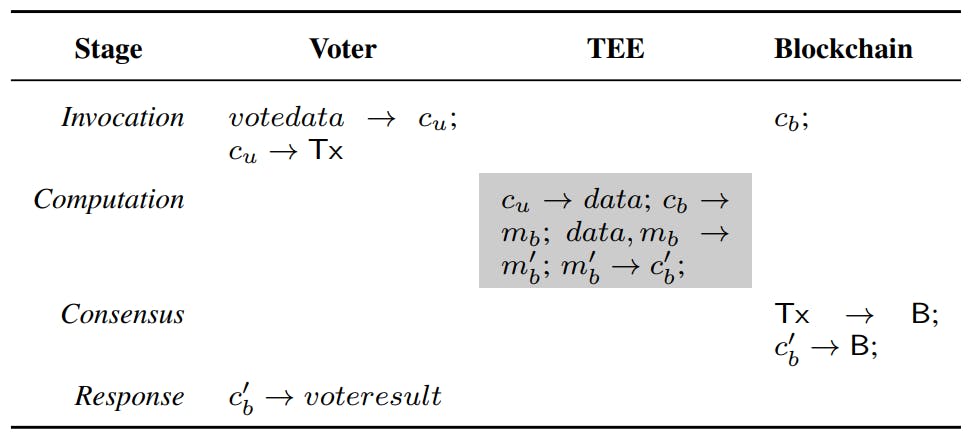
"The invocation, computation, consensus, and response steps are essential for establishing a confidential smart contract that operates securely."
A TCSC-based voting protocol operates securely through four main steps: invocation, computation, consensus, and response. It can function as a decentralized vote manager within an e-voting system, ensuring confidentiality, neutrality, auditability, and accountability. Voter inputs are encrypted, and computation takes place within Trusted Execution Environments to safeguard sensitive information. The voting logic is executed only when specific conditions are met, which maintains neutrality. Additionally, secured channels guarantee the confidentiality of transaction arguments, preventing unauthorized access by external attackers.
#blockchain #e-voting #confidential-smart-contracts #security-protocols #trusted-execution-environments
Read at Hackernoon
Unable to calculate read time
Collection
[
|
...
]